Lawyers need to understand what authenticator apps are to improve password security for logins. Of course, the first step to improve your security with online accounts is to use a password manager.
The next step is using two-factor authentication (2FA), but if you use an authenticator app you won’t need to use 2FA.
Why use authenticator apps?
Authenticator apps, like Google Authenticator, Microsoft Authenticator or Authy provide security that’s better than Two-Factor Authentication (2FA).
That’s because they generate valid verification codes regardless of whether your phone is online (unlike SMS-based two-factor authentication (2FA), which requires a cellular network to deliver a code).
How authenticator apps work
Time-Based One-Time Password
The primary method these apps use is a time-based one-time password (TOTP). This algorithm generates a one-time password based on the current time and a shared secret key.
Setting up the Authenticator
When you first set up an authenticator app for a particular service this what typically happens:
- The service provides a QR code.
- You scan this QR code with your authenticator app.
- This QR code encodes a shared secret key that’s specific to your user account on that service.
- Both the server (the online service) and your app now have the same shared secret, but it’s never exposed or sent over the internet again after the initial setup.
Generating the Time-Limited Codes
When you open the authenticator app, it uses the TOTP algorithm to generate a code. It does this by taking the shared secret and the current time as inputs and producing a 6-digit (usually) number as output.
The server knows your shared secret (from when you first set up the authenticator) and the current time.
So, when you log in and provide the 6-digit number, the server can replicate the TOTP algorithm on its end. If the code the server generates matches the code you input, it knows the login attempt is legitimate
The Limited Time Window
The generated codes are only valid for a short window of time, typically 30 seconds. After that, a new code is generated. This is why the codes in the app change periodically.
The server is aware of this time window, so even if an attacker manages to intercept or glimpse your code, it won’t be useful for very long.
Offline Operation
Since the code generation is based on a combination of the shared secret and the current time, and not on any communication with the server, your phone doesn’t need an internet or cellular connection to generate valid codes once the initial setup is complete.
Backup and Recovery
Some authenticator apps offer backup solutions, such as encrypted cloud backups or manual backup codes, to ensure you don’t lose access to your accounts if you lose your phone.
Use an Authenticator App on Two or More Devices
Contrary to widespread assumptions, you can indeed set up multi-device authentication with ease. To accomplish this, initiate the setup process on one device and, when presented with the QR code, scan it using your second device as well.
✅ Confirm that both applications generate matching codes.
For added security and convenience, print the QR code or save it as a PDF. This ensures that if you ever need to reconfigure your device, you’ll have ready access to the secret key shared with the server.
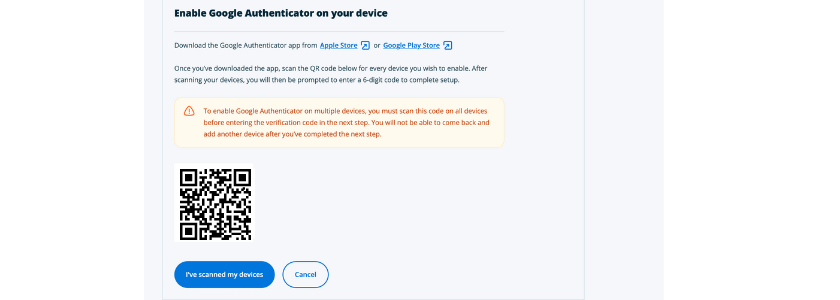
Here’s what you might see when you’re first enabling authentication through an authenticator app.
Note the warning that if you want to use it on more than one device you need to have them both ready to enter the verification code at the same time (which means you need to have them both ready as soon as you see a screen like this)>
Advantages Over SMS
Authenticator apps are generally considered more secure than SMS-based 2FA. SMS codes can be intercepted, especially if an attacker has convinced a mobile phone operator to redirect your text messages to them (a SIM swap attack).
Remember, SMS-based 2FA is not possible when you’re in an area with no cell reception.
Best Practices for Using Authenticator Apps
It’s essential to stick with just one authenticator app to avoid the confusion of keeping track of multiple apps for different websites. So, select one and use it for all your logins that require an authenticator app.
You might have the impression that a specific app doesn’t function with certain websites, but this is often a misunderstanding, possibly influenced by the authenticator app companies.
In reality, you can use any authenticator app for any website that supports the use of such apps.
Bottom Line
While 2FA using an authenticator app significantly increases account security, no method is 100% invulnerable.
Always be wary of phishing attempts and other social engineering methods that might be used to try to compromise your security.
Remember that one of the best tools to use to boost your cybersecurity protection is a password manager.
P.S. Get the Smart Lawyers Tech Guide.